WiMAX Network Architecture
- summary, description or overview of the basics of the WiMAX network architecture, detailing the different elements / entities in the WiMAX network.
WiMAX Wireless Broadband Technology Includes:
Basics & introduction
RF interface
WiMAX frequencies
MAC layer
Network architecture
The WiMAX network architecture defines the system after the air interface to enable a full end to end network to be achieved.
In order that elements of network equipment can be used from different suppliers, it is necessary to define the WiMAX network architecture that is common to all WiMAX networks. In this way economies of scale can be gained along with robust networks that are able to perform reliably under all conditions.
WiMAX network basics
The basic WiMAX standard does not define the WiMAX network for end to end connectivity. However the need for a standard WiMAX network architecture is realised and the WiMAX Forum Network Working Group have developed a standard for defining the WiMAX network architecture.
The standard now used is available from the WiMAX Forum as WiMAX Forum Network Architecture, document: WMF - T32-002-R010v04 and it is dated February 03, 2009.
WiMAX network architecture major entities
The WiMAX architecture developed by the WiMAX form supports is a unified network architecture to support fixed, nomadic and mobile operation. The WiMAX network architecture is based upon an all-IP model.
The WiMAX network architecture comprises three major elements or areas.
- Remote or Mobile stations: These are the user equipments that may be mobile or fixed and may be located in the premises of the user.
- Access Service Network, ASN : This is the area of the WiMAX network that forms the radio access network at the edge and it comprises one or more base stations and one or more ASN gateways.
- Connectivity Service Network, CSN: This part of the WiMAX network provides the IP connectivity and all the IP core network functions. It is what may be termed the core network in cellular parlance.
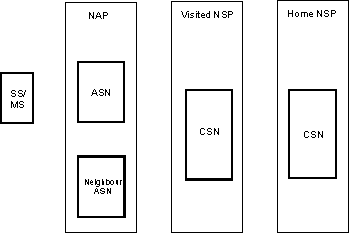
WiMAX network architecture
The overall WiMAX network comprises a number of different entities that make up the different major areas described above. These include the following entities
- Subscriber Station, SS / Mobile Station, MS : The Subscriber station, SS may often be referred to as the Customer Premises Equipment, CPE. These take a variety of forms and these may be termed "indoor CPE" or "outdoor CPE" - the terminology is self-explanatory. The outdoor CPE has the advantage that it provides better performance as a result of the better position of the antenna, whereas the indoor CPE can be installed by the user. Mobile Stations may also be used. These are often in the form of a dongle for a laptop, etc.
- Base Station, BS: The base-station forms an essential element of the WiMAX network. It is responsible for providing the air interface to the subscriber and mobile stations. It provides additional functionality in terms of micro-mobility management functions, such as handoff triggering and tunnel establishment, radio resource management, QoS policy enforcement, traffic classification, DHCP (Dynamic Host Control Protocol) proxy, key management, session management, and multicast group management.
- ASN Gateway, ASN-GW: The ASN gateway within the WiMAX network architecture typically acts as a layer 2 traffic aggregation point within the overall ASN.
The ASN-GW may also provide additional functions that include: intra-ASN location management and paging, radio resource management and admission control, caching of subscriber profiles and encryption keys. The ASN-GW may also include the AAA client functionality(see below), establishment and management of mobility tunnel with base stations, QoS and policy enforcement, foreign agent functionality for mobile IP, and routing to the selected CSN. - Home Agent, HA: The Home Agent within the WiMAX network is located within the CSN. With Mobile-IP forming a key element within WiMAX technology, the Home Agent works in conjunction with a "Foreign Agent", such as the ASN Gateway, to provide an efficient end-to-end Mobile IP solution. The Home Agent serves as an anchor point for subscribers, providing secure roaming with QOS capabilities.
- Authentication, Authorisation and Accounting Server, AAA: As with any communications or wireless system requiring subscription services, an Authentication, Authorisation and Accounting server is used. This is included within the CSN.
Wireless & Wired Connectivity Topics:
Mobile Communications basics
2G GSM
3G UMTS
4G LTE
5G
Wi-Fi
Bluetooth
IEEE 802.15.4
DECT cordless phones
Networking fundamentals
What is the Cloud
Ethernet
Serial data
USB
LoRa
VoIP
SDN
NFV
SD-WAN
Return to Wireless & Wired Connectivity