NFC Security
NFC security is very important, especially as it is used for payments & ticketing etc.
NFC, Near Field Communication Includes:
What is NFC?
NFC technology
NFC RF signal
Data exchange format
NFC Tags & tag types
NFC security
With electronic fraud and hacking increasing, NFC security is a matter of considerable importance.
With NFC being widely used for payments of various forms, it is essential that NFC is made highly secure.
NFC has security built into the system to enable very high levels of security to be achieved.
NFC security basics
There are several important areas for near field communications security. Each possibly vulnerability just be addressed and resolved. Some of the major NFC security areas are listed below:.
- Eavesdropping
- Data corruption
- Data modification
- Man-in-middle attack
These represent some of the ways in which NFC security could be compromised. Although the short range over which communications is possible reduces the possibility of any threats, it does not ensure complete NFC security, and as a result each NFC security issue must be addressed to ensure that it is not possible to breach.
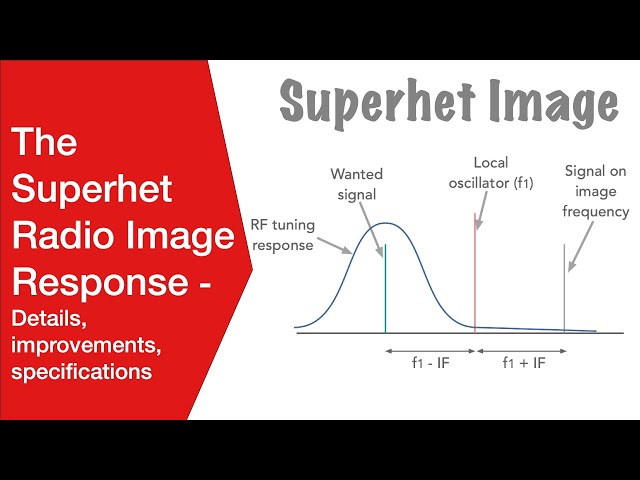
NFC security - Eavesdropping
Although near field communication is a short range technology - as the name implies - this does not make it immune to security attacks. As NFC uses radio waves to communicate, and these propagate in the vicinity of the transmitter, and not just to the wanted receiver, it is possible for unwanted users to pick up the signals. The technology to receive this signals is not difficult to create.
Although the range of NFC is limited to a few centimetres, it is still possible for a possible attacker to retrieve usable signals up to distances, often up to 1 metre away for passive signals, and for active mode distances of up to 10 metres may be at risk.
It is difficult to prevent eavesdropping as signals need to be reliably received by the required receiver and this requires a certain signal strength. An eavesdropper does not need to receive all communications - if only a percentage are received this may be adequate. Also the attacker may use large and sophisticated antennas - often logistics of the legitimate receiver at the point-of-sale terminal, etc may restrict the antenna size and performance. This requires signals to be sufficiently strong to ensure reliable communications.
The only real solution to prevent eavesdropping is to use a secure channel.
NFC security - data corruption
This near field communications security issue is essentially a form of denial of service attack. Rather than just listening to the communications, the attacker may try to disturb the communications by sending data that may be valid, or even blocking he channel so that the legitimate data is corrupted.
For this the attacker does not need to be able to decipher the valid data being sent.
It is possible for NFC devices to detect this form of NFC security attack. By listening when data is transmitted they will be able to detect any attack of this form because the power required to successfully attack a system is significantly higher than that which can be detected by the NFC device transmitting the data.
NFC security - data modification
This form of NFC security issue involves the attacker aiming to arrange for the receiving device to receive data that has been manipulated in some form. This data will naturally have to be in the correct format for it to be accepted.
This form of attack is possible for some bits under different coding schemes. There are a number of ways to provide protection against this form of security attack. It is impossible for an attacker to modify all the data transmitted at the 106 Baud data rate in active mode. As a result, the 106 Baud data rate, active mode would be required for data transfer in both directions. However this is the most vulnerable mode to eavesdropping.
The best option is to use a secure channel as this provides the greatest level of NFC security.
NFC security - man-in-the-middle
This form of NFC security issue involves a two party communication being intercepted by a third party. The third party acts as a relay, but using information received and modifying it if required to enable the attacker to achieve their aims. This must obviously be achieved without the two original parties knowing that there is an interceptor between them.

It is particularly difficult to achieve a man-in-the-middle attack on an NFC link. To completely minimise the risk, it is best to use an active-passive communication mode. In this way it would be possible to hear and detect any unwanted third party.
NFC secure channel
The best approach to ensuring NFC security is to use an NFC secure channel. This will protect against eavesdropping and data modification attacks.It is possible to use standard key agreement protocols such as Diffe-hellman because of the inherent protection has against man in the middle attacks. This protocol can be sued in the standard non-authenticated version because of the inherent NFC security.
The shared key can be used to derive a symmetric key which can then be used for the NFC secure channel.
The NFC secure channel provides for confidentiality, integrity and authenticity of the data transferred between devices.
Wireless & Wired Connectivity Topics:
Mobile Communications basics
2G GSM
3G UMTS
4G LTE
5G
Wi-Fi
Bluetooth
IEEE 802.15.4
DECT cordless phones
Networking fundamentals
What is the Cloud
Ethernet
Serial data
USB
LoRa
VoIP
SDN
NFV
SD-WAN
Return to Wireless & Wired Connectivity